VLAN Tagging on a local network
- The Asus RT-AX88U Pro Router supports VLAN tagging which allows for various advanced networking setups. In particular, VLAN tagging can be very useful when only a single Ethernet cable goes from a room to another, and you need to have different kinds of network traffic going through this cable (ie, WAN and LAN for instance).
- In addition, this router supports VLAN tagging on the WAN port, which basically means the WAN port can be used both for WAN (public Internet) traffic and LAN traffic. However, this feature is probably quite new and may be subject to some bugs.
- Another option to achieve the same setup would have been to use another smart switch on the end of the single Ethernet cable linking the switch to the router (although in this case, VLAN tagging on the WAN port, and even VLAN tagging altogether, does not need to be supported at all by the router, so it's a bit stupid to use an extensive router with this setup).
Setup
- You need to follow the exact steps described on this Asus page. They use as an example the exact setup I wanted to achieve (a single Ethernet cable linking the distribution room with a switch to a router that is placed in a more central area of the house).
- You will need a smart switch, ie a switch that can be configured and that supports VLAN tagging as well. I used the TP-Link TL-SG108E model.
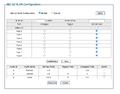
- In my case, I decided to use port 1 of the switch for the WAN traffic (so port 1 was connected to the modem), ports 2-5 for LAN devices and ports 6-8 were reserved on the default VLAN. Here is the configuration of the switch:
- Here is the configuration of the router (WAN tab):
Devices connected to the switch
- DHCP did not work correctly on the NAS connected to the switch (via dhcpcd on Debian). It was absolutely critical to setup manual IP assignment, else the NAS was no longer reachable (after a switch reboot). I believe something strange happened, maybe the device got a public IP (same issue than with the switch itself, see lower remark). In any case, once it reached that state, it was impossible to connect to it anymore, and since the NAS was headless, I could not investigate as much as needed, but removing DHCP fixed the problem entirely.
VLAN for guest networks
- You can setup totally separate subnetworks / LANs, and even different SSIDs (for Wifi). This can be useful
- On the Asus web configuration, you need to access the tab named "Guest Network Pro". Some of the configuration needs
Issues
- I managed to achieve the result I wanted, but manual IP address setup was required on a device connected to the switch (a Raspberry Pi 4 used as a NAS). Automatic setup via DHCP would not work correctly (if the connection to the switch was cut off, for instance by turning the switching off and on back again, the device was no longer pingable).
- Normally, it's better to separate the different VLANs you configured with separate sub networks. I don't know exactly how to achieve that properly yet (if at all possible with the Asus router), but I managed to get what I wanted without it in the end. In my cases, all devices should actually be reachable by any other, so there is only a single VLAN (the other one being used only to route traffic from the WAN).
TP-Link TL-SG108E Managed Switch
- It could happen that the switch interface / web server would get a public IP when asking for a DHCP lease. This is strange but is probably due to the fact that it is connected directly to the cable modem acting in bridge mode, so somehow the switch was mistaken for a router. To fix this, I entered a static IP and gateway for the switch, rather than relying on DHCP.